SilentBanker is one of the serious threats as most of the banking Trojan does. It uses many variety of techniques such as HTML injection and replacement, cookie stealing, certification stealing. This provides the capabilities of SilentBanker. It also present details on how to detect the Trojan on an infected system. This provides an in depth analysis of Trojan SilentBanker by taking a one of the sample (sdra64.exe) of it. This explains the SilentBanker functionally, characteristic, method of infection and detection, and removal. This also describes the Trojan SilentBanker, the resources and environment used for analysis, the method and techniques used for total reverse engineer and some of the analysis troubles found and their solutions. It also presents some best practices to use while reverse code engineering (Behavioral Analysis). This Trojan is an executable program unlike viruses, Trojans do not replicate itself. They are distributing manually, frequently under the principle that attackers are beneficial or wanted. The execution of these Trojan results in system or security exploitation, and unsuspecting user executes the program with their knowledge. Channel which they spread includes email, malicious or hacked web sites, peer to peer networks, Internet Relay Chat (IRC), and many more.
Infection and Installation Method
One of the possible methods to spread is by clicking links in spam emails which contains the malicious binaries and malware installed just by clicking on the executables (sdra64.exe).Viruses are not considered to be as password stealers and they do not replicate themselves.
The other possible method might be just visiting a malicious web sites .i.e. by going a link hosting a scripted exploit where password stealer can get installed on to the users system without user knowledge.After the execution of this Trojan, it creates some of files to collect information and save the encrypted configuration of the Trojan.
%SysDir%\lowsec\local.ds – configuration file
% SysDir%\lowsec\user.ds – log file
Next, this Trojan makes entries in registry, so that it can execute at every time when Windows starts:
-- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\"userinit" = "%System%\ sdra64.exe"
-- HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Run\"userinit" = "%System%\ sdra64.exe"
It alters following registry entries in order that it executes every time Windows starts:
-- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsNT\CurrentVersion\Winlogon\
-- "Userinit" = "%System%\userinit.exe, %System%\sdra64.exe"
Next the listed processes are injected by the malicious code:
WINLOGON.EXE
SVCHOST.EXE
Now we have abstract idea about the Trojans infection and its installation, and following section shows how it can detected by using some tools.
Reversing SilentBanker
The Trojan PWS-Banker.cz is an executable program (sdra64.exe) that introduces additional Trojan code on the host system. This dropper is frequently the first module to execute in a sequence of infections. It downloads rootkit drivers form the internet once when it is in action, it also get dynamic link library (DLL) or configuration files that attackers compiled into it Trojan program. This technique will bring in a smaller Trojan dropper, but one that needs network activity to load the remainder of the required attack files. This section explains executable that leads to installation of SilentBanker.
Once it executed it well inject code into the svchost.exe, this can be observed through TCPview. See the below snap short taken form TCPView .i.e. it have injected its code in svchost.exe.
Once it executed it well inject code into the svchost.exe, this can be observed through TCPview. See the below snap short taken form TCPView .i.e. it have injected its code in svchost.exe.

Then Trojan is trying to connect to the IP address 91.212.41.250 of basdzsdas.com server, this was observed through wireshark. Check the below snapshot: When try to resolve to IP 91.212.41.250 to download config.bin file. Configuration file happens to be encrypted. Check the below snapshot.
When try to resolve to IP 91.212.41.250 to download config.bin file. Configuration file happens to be encrypted. Check the below snapshot.
One of the characteristic of this Trojan is to update itself by checking the updated copy at basdzsdas.com/poker/loader.exe. It also collects information from the system upload to basdzsdas.com/poker/snd.php, this file is also encrypted. Check the below two snapshots.

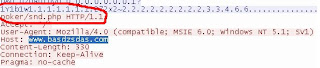
Now when we check for registry entry in autostart:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsNT\CurrentVersion\Winlogon\"Userinit" = "%System%\userinit.exe, %System%\sdra64.exe"
Now we read memory dumb of svchost using WinHex tool and search for a string “bank”. We search the list of bank which was targeted such as “bankofAmerica.com “
The decryption code is incorporated into the main executable, which is capable of decrypting it. Currently we don’t have the algorithm, but we can see the decrypted code in memory. Config.bin mainly contains the various banks to be targeted. So, for this reason we look for string “bank”. Finally we check for rootkit, the folder called “lowsec” and few files inside that.
Finally we check for rootkit, the folder called “lowsec” and few files inside that. Now if we use the internet explorer browser to banking website .i.e. to check for Trojan SilentBanker reaction, we can see display of fake bank login.
Now if we use the internet explorer browser to banking website .i.e. to check for Trojan SilentBanker reaction, we can see display of fake bank login.
No comments:
Post a Comment